

The mastodon version of a post or, sadly, tweet.
It’s, uh, not the best name.
But maybe, just maybe, it more appropriately attributes correct value to a social media thing. ;)


The mastodon version of a post or, sadly, tweet.
It’s, uh, not the best name.
But maybe, just maybe, it more appropriately attributes correct value to a social media thing. ;)


If it’s a backup server why not build a system around an CPU with an integrated GPU? Some of the APUs from AMD aren’t half bad.
Particularly if it’s just your backup… and you can live without games/video/acceleration while you repair your primary?


I’ve been using self-hosted Ghost for a bit and it’s a pretty well designed piece of software.
That it requires mailgun to really function well was a bit of a nuisance. But that’s a very minor nitpick that will likely change if adoption increases.


Pros:
Cons:
I’m on iOS and do the same thing.
The WireGuard app has a setting to “connect on demand”. It’s in the individual connections/configurations.
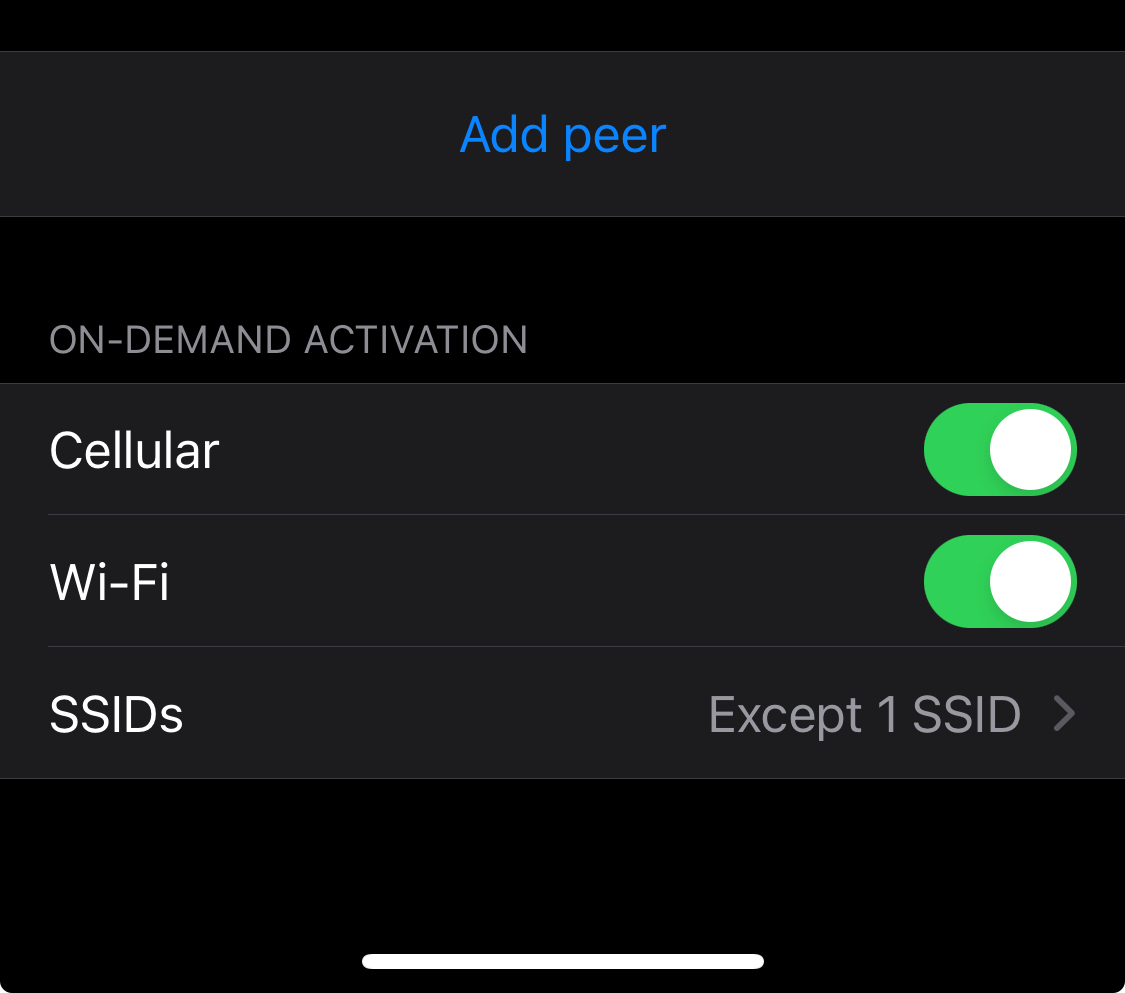
You can then set either included or excluded SSIDs. There’s also an option to always connect when you’re on mobile/cellular data.
I imagine the Android app is similar.


DM’ed you the link.
Reason: personal GitHub account.


Reddit was aggressively rate limiting tools used to delete and edit content in a funny way when the API pricing was announced. The API wouldn’t return an error, the rate limiting was silent, and the tools would report successful deletion or edits even when the edit or deletion wasn’t made.
I had to modify an existing script to handle the 5-second rate limit and, lieu of deleting, I just rewrote each comment with a farewell.
Even then I did 3 passes (minor additional edits) in cases Reddit was saving previous edits.
My content has stayed edited.


Neat, I’ll have to look it up. Thanks for sharing!


Nextcloud isn’t exposed, only a WireGuard connection allows for remote access to Nextcloud on my network.
The whole family has WireGuard on their laptops and phones.
They love it, because using WireGuard also means they get a by-default ad-free/tracker-free browsing experience.
Yes, this means I can’t share files securely with outsiders. It’s not a huge problem.


In many cases a lot of sites don’t make it clear that they have a conflict of interest.
You want to push a product on me and you’ll get a cut? Cool, but disclose that.


Update: I went and had a look and there’s a Terraform provider for OPNSense under active development - it covers firewall rules, some unbound configuration options and Wireguard, which is definitely more than enough to get started.
I also found a guide on how to replicate pfBlocker’s functionality on OPNSense that isn’t terribly complicated.
So much of my original comment below is less-than-accurate.
OPNSense is for some, like me, not a viable alternative. pfBlockerNG in particular is the killer feature for me that has no equivalent on OPNSense. If it did I’d switch in a heartbeat.
If I have to go without pfBlockerNG, then I’d likely turn to something that had more “configuration as code” options like VyOS.
Still, it’s nice to know that a fork of a fork of m0n0wall can keep the lights on, and do right by users.


If you backup your config now, you’d be able to apply the config to CE 2.7.x.
While this would limit you to an x86 type device, you wouldn’t be out of options.
I am an owner of an SG-3100 as well (we don’t use it anymore), but that device was what soured me on Netgate after using pfSense on a DIY router at our office for years…
I continued to use pfSense because of the sunk costs involved (time, experience, knowledge). This is likely the turning point.


Cluster of Pi4 8GBs. Bought pre-pandemic; love the little things.
Nomad, Consul, Gluster, w/ TrueNas-backed NFS for the big files.
They do all sorts of nifty things for us including Nightscout, LanguageTool OSS, monitoring for ubiquiti, Nextdrive, Grafana (which I use for home monitoring - temps/humidity with alerts), Prometheus & Mimir, Postgres, Codeserver.
Basically I use them to schedule dockerized services I want to run or am interested in playing with/learning.
Also I use Rapsberry Pi zero 2 w’s with Shairport-sync (https://github.com/mikebrady/shairport-sync ) as Airplay 2 streaming bridges for audio equipment that isn’t networked or doesn’t support AirPlay 2.
I’m not sure I’d buy a Pi4 today; but they’ve been great so far.


Discomfort can be a good thing; change is often uncomfortable.
But that’s a far cry from being tortured and it sounds like that’s what Musk does to the people around him; using platitudes and words of wisdom as weapons of control and coercion.
As someone who runs a self-hosted mail service (for a few select clients) in AWS, this comment ring true in every way.
One thing that saved us beyond SPF and DKIM was DMARC DNS records and tooling for diagnosing deliverability issues. The tooling isn’t cheap however.
But even then, Microsoft will often blacklist huge ranges of Amazon EIPs and if you’re caught within the scope of that range it’s a slow process to fix.
Also, IP warming is a thing. You need to start slow and at the same time have relatively consistent traffic levels.
Is it worth it, not really no - and I don’t think I’d ever do it again.


deleted by creator
The only way to ensure privacy is something like PGP. Encrypt before you send. Heck you could even encrypt before you put the contents into a message body.
With self hosted, the messages themselves aren’t encrypted at rest and they are clear text between hops even if those hops support TLS in transit.
Ultimately the right answer for you will hinge on what your definition and level of privacy is.


They do indeed: https://httptoolkit.com/blog/apple-private-access-tokens-attestation/
From the article:
The focus here is primarily on removing captchas, and as such it’s been integrated into Cloudflare (discussed here) and Fastly (here) as a mechanism for recognizing ‘real’ clients without needing other captcha mechanisms.
Fundamentally though, it’s exactly the same concept: a way that web servers can demand your device prove it is a sufficiently ‘legitimate’ device before browsing the web.


As someone who’s working for their third VC-backed firm, I took the previous comment to mean that the VC money was used to grow the company knowingly in the red, like many growth-stage, VC-funded businesses.
Heck a fair number of post-IPO tech firms continue to operate in the red as a result of their share sales.
TIL - thanks!