

I really enjoyed my time with it, even though I’ve not played many games in this “style”.
The campaign is quite lengthy even though it’s not finished yet, so you’ll definitely get your money’s worth.
I made LASIM! https://github.com/CMahaff/lasim
I currently have 3 accounts (big shock):


I really enjoyed my time with it, even though I’ve not played many games in this “style”.
The campaign is quite lengthy even though it’s not finished yet, so you’ll definitely get your money’s worth.
Sounds like a problem with Memmy. Does this link work? https://lemm.ee/c/sfah@hilariouschaos.com
You should be able to search communities in your app and could have searched “sfah@hilariouschaos.com” too.
But basically communities on Lemmy are in the form of “name@host”. The “name” can be whatever someone wants, and the “host” is the website / Lemmy instance where that community originates from. But because it is federated it’s all available everywhere (generally speaking). For example, if you visit https://lemmy.world/c/sfah@hilariouschaos.com it should be the same content just loaded via lemmy.world instead of lemme.ee. However if theoretically someone went and made a “sfah@lemmy.world” community, that would be a completely separate community from the above, hosted on a different Lemmy instance.


I’ll just add that another, albeit smaller, category of games that don’t work are really new, demanding titles. There’s not a lot of them for now, but naturally the deck wasn’t the most powerful device to begin with and over time less titles will work well.
Starfield was pointed out to me as an example of one that can’t run on the deck for performance reasons (not that Bethesda is known for their optimization) and BG3 was only barely playable at the lowest settings in the more demanding areas of the game (i.e. Act 3).
That said, for its price point, and considering most games are using the proton compatibility later, I was actually very impressed with its performance.


Found a blog post that gives a quick overview of how to do git via email in general: https://peter.eisentraut.org/blog/2023/05/09/how-to-submit-a-patch-by-email-2023-edition
So at least from my understanding you’d make your changes, email the contents of the patch to the maintainer, and then they’d apply it on their side, do code review, email you comments, etc. until it was in an acceptable state.
There’s also the full kernel development wiki that goes into all the specifics: https://www.kernel.org/doc/html/v4.16/process/howto.html
(I never got through the whole thing)


I’ll also throw out: aging infrastructure, build systems, coding practices, etc.
I looked into contributing to the kernel - it’s already an uphill battle to understand such a large, complex piece of software written almost entirely in C - but then you also need to subscribe to busy mailing lists and contribute code via email, something I’ve never done at 30 and I’m betting most of the younger generation doesn’t even know is possible. I know it “works” but I’m really doubting it’s the most efficient way to be doing things in 2024 - there’s a reason so many infrastructure tools have been developed over the years.
The barriers to entry for a lot of projects is way too high, and IMO a lot of existing “grey” maintainers, somewhat understandably, have no interest in changing their processes after so much time. But if you make it too hard to contribute, no one will bother.


I’m surprised by Helldiver’s. Has there been some performance patches? I tried playing that on my deck near launch and it really struggled even at minimum settings - I can’t imagine how it would run at higher difficulties.


Out of curiosity, what switch are you using for your setup?
Last time I looked, I struggled to find any brand of “home tier” router / switch that supported things like configuring vlans, etc.


Maybe I am not thinking of the access control capability of VLANs correctly (I am thinking in terms of port based iptables: port X has only incoming+established and no outgoing for example).
I think of it like this: grouping several physical switch ports together into a private network, effectively like each group of ports is it’s own isolated switch. I assume there are routers which allows you to assign vlans to different Wi-Fi access points as well, so it doesn’t need to be literally physical.
Obviously the benefits of vlans over something actually physical is that you can have as many as you like, and there are ways to trunk the data if one client needs access to multiple vlans at once.
In your setup, you may or may not benefit, organizationally. Obviously other commenters have pointed out some of the security benefits. If you were using vlans I think you’d have at a minimum a private and public vlan, separating out the items that don’t need Internet access from the Internet at all. Your server would probably need access to both vlans in that scenario. But certainly as you say, you can probably accomplish a lot of this without vlans, if you can aggressively setup your firewall rules. The benefit of vlans is you would only really need to setup firewall rules on whatever vlan(s) have Internet access.


This was my experience as well, though I did notice that many games did not properly isolate game saves from separate steam accounts.
Tip to any devs that might read this: organize saves based on the steam account logged in, not the user of the PC (always “deck” for the steam deck) and definitely not just a single location among the game’s data.


I ran into the same thing. I’ve always just worked around it, but I believe I did find the solution at one point (can’t find the link now).
But if I am remembering right, I believe you need to manually create a bridge between the two networks - by default it isolates the VMs from TrueNAS itself for security reasons.
Sorry I can’t link the exact fix right now, but hopefully this will help you Google the post I found on the subject.


Absolutely this. There are issues with deletes not federating properly too, right?
That’s a big part of the issue here too since even when .world cleans up the content it’s already been pushed out to every other instance and will now remain there until all THOSE admins also purge it.

That link seems to 404. I will IM you shortly.

Sure thing.
Do you get any additional information in your error log?
If not, would you be open to running a version with additional debugging statements to help identify the cause of the failures?
I know there is an issue when .world is overloaded where this happens, but if it’s happening constantly it has to be something specific with your account vs mine.

LASIM author here - there does not appear to be any API changes in 0.18.4, and it seemed to work fine with my testing.
I’ve updated the table on the Github README to reflect this.


This is now released :)


For anyone finding this in the future:
The latest version of LASIM (0.2.1) has a Settings tab that allows you to choose what you want to upload.
If you are using the JSON file posted above, you’d want to choose just “Upload Community Subscriptions” on this tab so that your profile settings, etc. are not changed.


Sneak peek :)
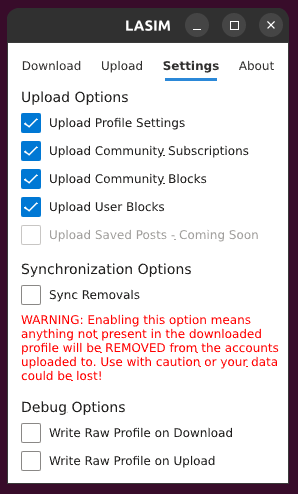


I hadn’t even considered this use case for LASIM, but that’s really neat.
I’ve been thinking about a settings page where you can toggle what to sync, among a few other future features. I’ll definitely add an option in the future to NOT sync the profile settings.


LASIM author here - you are correct. I explicitly made it “additive” to avoid accidents where you could end up erasing a bunch of subscriptions. Right now LASIM only calls the subscribe API interface so it’s actually impossible for it to unsubscribe you from anything.
I am considering adding a “destructive” sync in the future which, if toggled on, would unsubscribe you from anything not in the JSON file. But it’s not implemented yet!
Doubling what Klaymore said, I’ve seen this “just work” as long as all partitions have the same password, no key files necessary.
That said, if you needed to use a key file for some reason, that should work too, especially if your root directory is one big partition. Keep in mind too that the luks commands for creating a password-based encrypted partition vs a keyfile-based encrypted partition are different, so you can’t, for example, put your plaintext password into a file and expect that to unlock a LUKS partition that was setup with a password.
But the kernel should be trying to mount your root partition first at boot time where it will prompt for the password. After that it would look to any /etc/crypttab entries for information about unlocking the other partitions. In that file you can provide a path to your key file, and as long as it’s on the same partition as the crypttab it should be able to unlock any other partitions you have at boot time.
It is also possible, as one of your links shows, to automatically unlock even the root partition by putting a key file and custom /etc/crypttab into your initramfs (first thing mounted at boot time), but it’s not secure to do so since the initramfs isn’t (and can’t be) encrypted - it’s kind of the digital equivalent of hiding the house key under the door mat.